Self-sovereign identities with verifiable claims
By Nabil MELLAL
Jan 23, 2019
- Categories
- Data Governance
- Tags
- Authentication
- Blockchain
- Cloud
- IAM
- Ledger [more][less]
Never miss our publications about Open Source, big data and distributed systems, low frequency of one email every two months.
Towards a trusted, personal, persistent, and portable digital identity for all.
Digital identity issues
Self-sovereign identities are an attempt to solve a couple of issues. The first is the acknowledgment that even with the pervasive use of digital services, we still don’t have a digital ID. We have accounts, hundreds of them (ever searched for “best multi-platform password manager”?), some representing us better than others, some more useful than others. But at the end of the day, they are not our ID, they are not even ours. Those accounts are owned by the provider, allowing us to use the service, in exchange for the data and information we provide. Which brings us to the second issue: trust.
How did we get where we are now and how do self-sovereign identities fit in the picture?
The story of the 3 models
Most of the concepts are detailed in the blog entry “The Path to Self-Sovereign Identity” by Christopher Allen. “The Three Models of Digital Identity Relationships” is also a good read.
To make a long story short, digital identities started with a siloed, centralized identity model, your Google or Microsoft account for example. The architecture then moved to a federated identity, where you can use your Facebook account to log in to any other service, leading to less login/passwords, but adding a new layer of trust. Thus, still no total control of your personal information: you can log in to GitLab using your GitHub account, even move your projects, but what about your stars? your reputation? is one example.
The third wave is self-sovereign identities, coming with a quite simple set of goals: remove the middleman and give the holder complete control. I will cite Evernym:
“Self-Sovereign Identity, or SSI, is the latest digital identity model which allows any person or organization to maintain complete control of their identity and utter independence from intermediaries. It is safe, secure, portable and cannot be taken away. This makes it an ideal model to safeguard the identity information of the disenfranchised.”
The goals
The goals are detailed by Allen in its 10 principles of self-sovereign identity:
- Existence: Users must have an independent existence
- Control: Users must control their identities
- Access: Users must have access to their own data
- Transparency: Systems and algorithms must be transparent
- Persistence: Identities must be long-lived
- Portability: Information and services about identity must be transportable
- Interoperability: Identities should be as widely usable as possible
- Consent: Users must agree to the use of their identity.
- Minimalization: Disclosure of claims must be minimized.
- Protection: The rights of users must be protected.
The implementation
How is it being implemented?
Nearly a year ago, an NGO (CIRID), asked me to look at a way to provide diaspora members with digital identities. Around the same time, Microsoft and Accenture announced their project to provide refugees with blockchain-based digital IDs. Then, a couple of months ago, Evernym and the Sovrin Foundation, in collaboration with the World Economic Forum, announced forming the Identity For Good initiative, both projects related to self-sovereign identities.
An actual running implementation is led by the Sovrin foundation, using a public permissioned blockchain as a ledger. Sovrin managing the constitution, while the infrastructure is operated by organizations who agreed to abide by that constitution, called stewards. Most of the work has been open-sourced as the hyperledger indy project.
There are some other implementations like uPort, ShoCard.
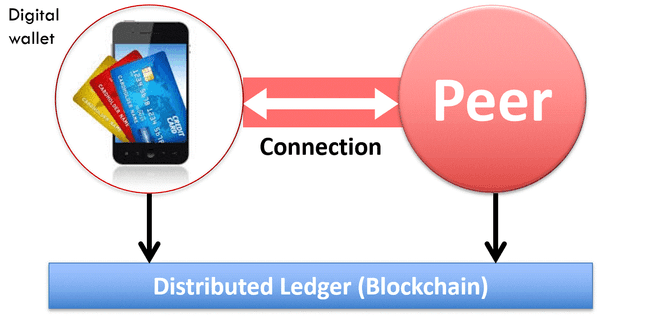
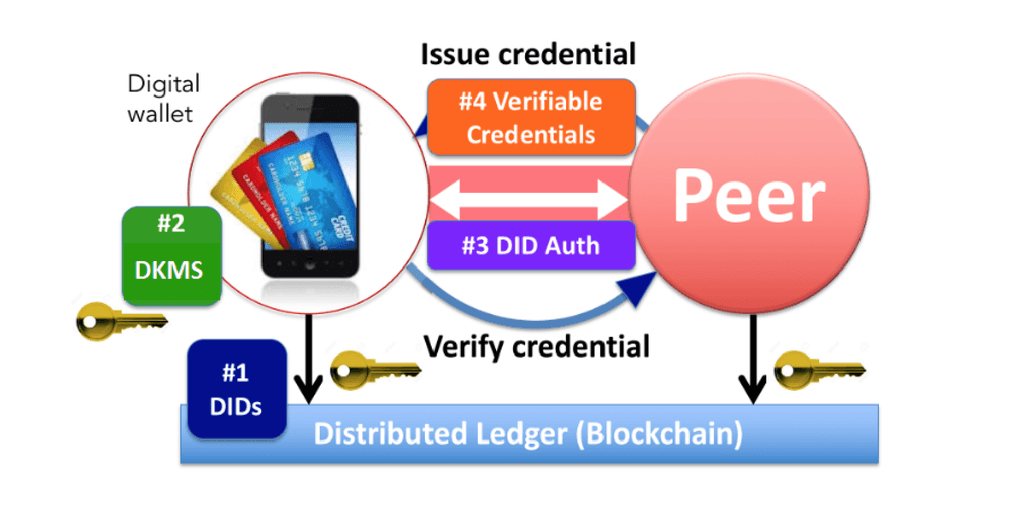
Conceptually, you can think of it as a digital wallet containing all your credentials and claims. The claims are provided and signed by peers in the network, you can share them with other peers. The associated public key is stored on a global public ledger. The ledger doesn’t store the claims.
To make this possible, a couple of standards are emerging:
- DIDs, Distributed Identifiers, which can be seen as an address to a public key in a public ledger;
- DKMS, for a standardized distributed key management system;
- [DID Auth](https://github.com/WebOfTrustInfo/rebooting-the-web-of-trust-spring2018/blob/master/topics-and-advance-readings/DID-Auth protocol.md), for authentication during a session with a peer;
- Verifiable claims
Conclusion
Digital transformation, privacy scandals, and massive security breaches make an overhaul of the identities management necessary, essentially for us users. Sovereign identities bring interesting approaches to fundamental problems. From a technical perspective and implementation, projects like hyperledger indy would greatly benefit from the experience of other large Open Source projects.