Cybersécurité
Protection des appareils, des réseaux et des applications contre le vol et les dommages sur les données et les services.
Articles associés

GUI applications in the terminal with Term.Everything❗
Catégories : Cyber Security, Hack | Tags : Bash, Shell, Security, SSL/TLS
Term.Everything❗ enables the execution of GUI applications directly within the terminal environment. The functionality allows you to run applications such as Firefox from a remote server over SSH. The…
Par David WORMS
16 sept. 2025

Keyser, single bash script for SSL certificates management
Catégories : Cyber Security, DevOps & SRE | Tags : Bash, Cyber Security, DevOps, Encryption, SSL/TLS
Keyser is a command-line utility designed to streamline the creation, management, and protection of SSL certificates with security and efficiency. Distributed as a single Bash script, it provides…
Par Eliott MORCILLO
25 juin 2025

Buttercup to KeePass exporter
Catégories : Cyber Security | Tags : Authentication, CSV, Node.js
Buttercup is a password manager which works on all major platforms including Linux, macOS, Windows, iOS and Android. On March 3rd, Buttercup’s main contributor Perry Mitchell announced the retirement…
Par David WORMS
14 mai 2025

OAuth2 and OpenID Connect for microservices and public applications (Part 2)
Catégories : Containers Orchestration, Cyber Security | Tags : LDAP, Micro Services, CNCF, JavaScript Object Notation (JSON), OAuth2, OpenID Connect
Using OAuth2 and OpenID Connect, it is important to understand how the authorization flow is taking place, who shall call the Authorization Server, how to store the tokens. Moreover, microservices and…
Par David WORMS
20 nov. 2020

OAuth2 and OpenID Connect, a gentle and working introduction (Part 1)
Catégories : Containers Orchestration, Cyber Security | Tags : Go Lang, JAMstack, LDAP, CNCF, Kubernetes, OAuth2, OpenID Connect
Understanding OAuth2, OpenID and OpenID Connect (OIDC), how they relate, how the communications are established, and how to architecture your application with the given access, refresh and id tokens…
Par David WORMS
17 nov. 2020

Policy enforcing with Open Policy Agent
Catégories : Cyber Security, Data Governance | Tags : Kafka, Ranger, Authorization, Cloud, Kubernetes, REST, SSL/TLS
Open Policy Agent is an open-source multi-purpose policy engine. Its main goal is to unify policy enforcement across the cloud native stack. The project was created by Styra and it is currently…
Par Leo SCHOUKROUN
22 janv. 2020

Kerberos and Spnego authentication on Windows with Firefox
Catégories : Cyber Security | Tags : Firefox, HTTP, FreeIPA, Kerberos
In Greek mythology, Kerberos, also called Cerberus, guards the gates of the Underworld to prevent the dead from leaving. He is commonly described as a three-headed dog, a serpent’s tail, mane of…
Par David WORMS
4 nov. 2019
Apache Knox made easy!
Catégories : Big Data, Cyber Security, Adaltas Summit 2018 | Tags : LDAP, Active Directory, Knox, Ranger, Kerberos, REST
Apache Knox is the secure entry point of a Hadoop cluster, but can it also be the entry point for my REST applications? Apache Knox overview Apache Knox is an application gateway for interacting in a…
Par Michael HATOUM
4 févr. 2019

Managing User Identities on Big Data Clusters
Catégories : Cyber Security, Data Governance | Tags : LDAP, Active Directory, Ansible, FreeIPA, IAM, Kerberos
Securing a Big Data Cluster involves integrating or deploying specific services to store users. Some users are cluster-specific when others are available across all clusters. It is not always easy to…
Par David WORMS
8 nov. 2018
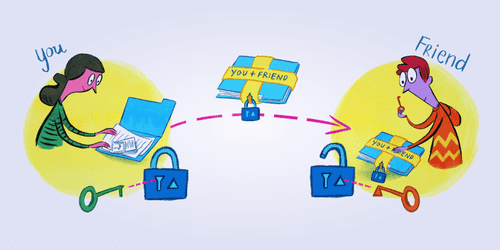
Guide to Keybase encrypted directories
Catégories : Cyber Security, Hack | Tags : Cryptography, Encryption, File system, Keybase, PGP, Authorization
This is a guide to using Keybase’s encrypted directories to store and share files. Keybase is a group, file and chat application who’s goal is to bring public key crypto based on PGP to everyone in…
Par Arthur BUSSER
18 juin 2018

Apache Metron in the Real World
Catégories : Cyber Security, DataWorks Summit 2018 | Tags : Algorithm, Solr, Storm, pcap, RDBMS, HDFS, Kafka, Metron, NiFi, Spark, Data Science, Elasticsearch, SQL
Apache Metron is a storage and analytic platform specialized in cyber security. This talk was about demonstrating the usages and capabilities of Apache Metron in the real world. The presentation was…
Par Michael HATOUM
29 mai 2018

Remote connection with SSH
Catégories : Cyber Security | Tags : Automation, HTTP, SSH
While teaching Big Data and Hadoop, a student asks me about SSH and how to use. I’ll discuss about the protocol and the tools to benefit from it. Lately, I automate the deployment of Hadoop clusters…
Par David WORMS
2 oct. 2013
Kerberos and delegation tokens security with WebHDFS
Catégories : Cyber Security | Tags : HTTP, HDFS, Big Data, Kerberos
WebHDFS is an HTTP Rest server bundle with the latest version of Hadoop. What interests me on this article is to dig into security with the Kerberos and delegation tokens functionalities. I will cover…
Par David WORMS
25 juil. 2013